Best Practices for Keeping Data Safe: Insights from a CompTIA Webinar

Hello everyone, I'm Tycho Loke from PeopleRock, based in the Benelux region. As the Vice Chair of the Cyber Security Interest Group at CompTIA, I recently participated in a webinar where I discussed essential practices for maintaining data security, focusing particularly on data classification and access control. In this blog post, I'll share the key points from my presentation and provide actionable steps for your organization to enhance its data protection measures.
Importance of Data Classification for AI and AI Prompting
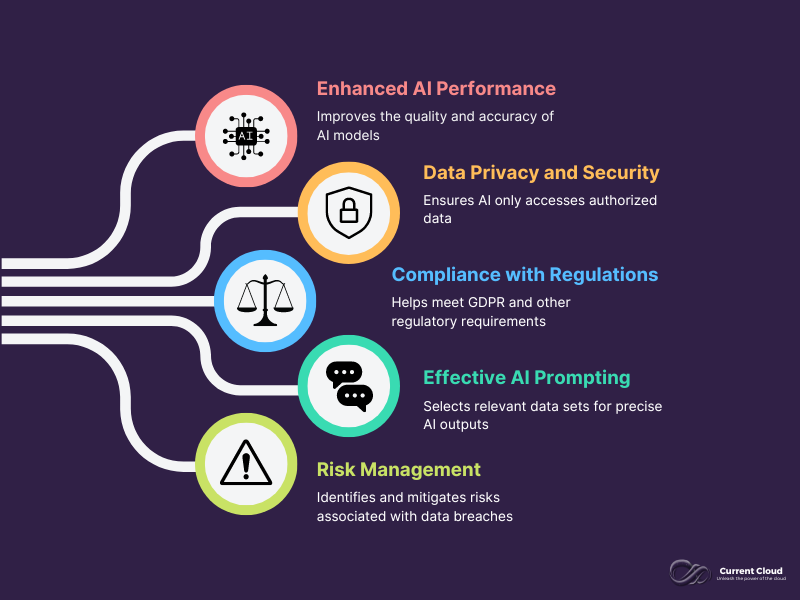
Data classification isn't just an organizational tool; it's a critical component in ensuring the security and effectiveness of AI systems. Here's why data classification is essential:
- Enhanced AI Performance: Well-classified data improves the quality and accuracy of AI models, ensuring that the insights and predictions generated are reliable and relevant.
- Data Privacy and Security: Data classification helps enforce strict access controls, ensuring AI only accesses data it is authorized to handle, thus protecting sensitive information from unauthorized access or misuse.
- Compliance with Regulations: With stringent data protection laws like GDPR, data classification ensures that AI systems comply with regulatory requirements by categorizing data based on legal mandates.
- Effective AI Prompting: Proper data classification aids in selecting the most relevant data sets for AI prompting, enhancing the system’s ability to deliver precise and useful outputs.
- Risk Management: Understanding the sensitivity levels of different data types allows organizations to design AI systems that prioritize the protection of the most critical information.
What is Data Classification?
Data classification is the process of organizing data into categories that make it easier to manage, protect, and use. It involves assigning a level of sensitivity to data, which dictates how it should be handled and who should have access to it. Proper data classification helps organizations:
- Ensure data security by applying appropriate protection measures.
- Comply with legal and regulatory requirements.
- Enhance data management efficiency.
- Improve the accuracy and effectiveness of AI systems.
Forms of Data Classification
Data classification typically falls into a few key forms:
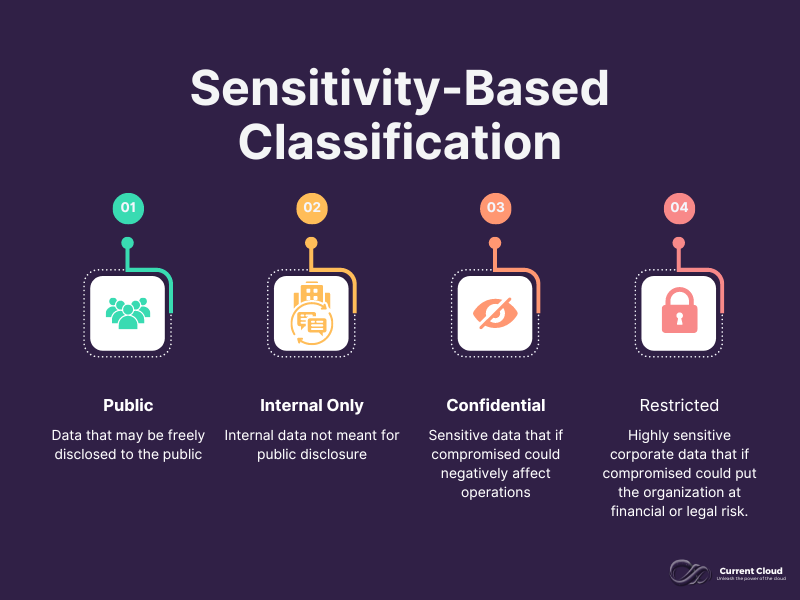
- Sensitivity-Based Classification:
- Public Data: Information that can be freely shared without any risk, such as marketing materials.
- Internal Data: Information meant for internal use, like internal emails.
- Confidential Data: Sensitive information needing protection, like customer details or financial records.
- Restricted Data: Highly sensitive data requiring strict controls, such as trade secrets or personal identifiable information (PII).
- Regulatory-Based Classification:
- GDPR Data: Personal data of EU citizens that must comply with the General Data Protection Regulation (GDPR).
- ePrivacy Data: Information complying with the EU's ePrivacy Directive, dealing with electronic communications privacy.
- Local Data Protection Laws: Data adhering to specific national regulations within the Benelux region, like the Dutch Data Protection Act (DPA).
- Business-Criticality Classification:
- Mission-Critical Data: Information essential for the operation of the organization.
- Business-Important Data: Important data for the business but not critical to daily operations.
- Operational Data: Routine data used in day-to-day operations.
Examples of Data Classification
To illustrate these forms, let's go through some practical examples:
- Sensitivity-Based Classification:
- A company’s quarterly financial report is classified as confidential.
- Employee manuals are classified as internal data.
- Company brochures are public data.
- Regulatory-Based Classification:
- Customer names and addresses collected in the EU are classified under GDPR data.
- Data related to online marketing activities is classified under ePrivacy data.
- Personal data processed by a Dutch company is classified under the Dutch Data Protection Act.
- Business-Criticality Classification:
- The source code for a software company’s flagship product is mission-critical data.
- Marketing plans for next quarter are business-important data.
- Routine correspondence and memos are operational data.
Where to Apply Data Classification
Data classification can be applied across various domains within an organization in the Benelux region:
- Enterprise Data Management:
- Organizing and managing data assets in data warehouses and data lakes.
- Compliance and Legal:
- Ensuring data handling practices meet regulatory requirements, especially GDPR.
- Security Operations:
- Enhancing threat detection and response by understanding data sensitivity levels.
- Human Resources:
- Protecting employee personal information and performance records.
- Customer Relationship Management:
- Safeguarding customer data and ensuring privacy compliance.
- Safeguarding customer data and ensuring privacy compliance.
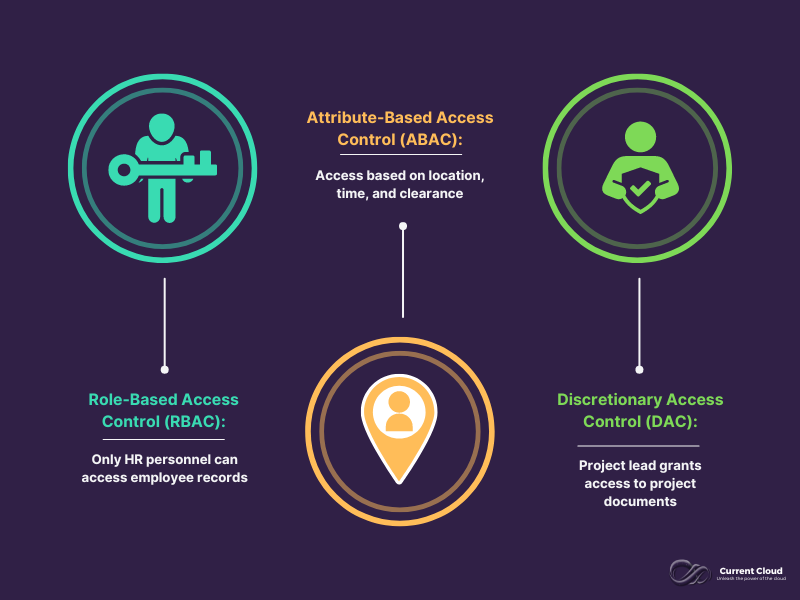
Access Control and Data Classification
Access control determines what users can access and what actions they can perform. It is closely linked with data classification because the sensitivity and criticality of data dictate the level of access control required.
- Role-Based Access Control (RBAC):
- Assigns permissions based on the user's role within the organization. For instance, only HR personnel can access employee records classified as confidential.
- Attribute-Based Access Control (ABAC):
- Grants access based on attributes such as user location, time of access, and data classification. For example, only users with the appropriate security clearance can access restricted data.
- Discretionary Access Control (DAC):
- The data owner decides who has access to specific data. For example, a project lead might grant access to project documents classified as business-important.
AI and Access Control
Incorporating AI into access control can enhance security by dynamically adjusting access rights based on real-time analysis and contextual data. However, it’s crucial to ensure that AI systems adhere to the same access control policies as human users. Properly configured access controls ensure that both human and AI users interact with data safely and appropriately.
Be Aware of Freeware AI Tools
It's also important to be cautious about the freeware AI tools you use. Here are some considerations:
- Where is My Data Processed?: Understand where your data is being processed. Ensure that the data is stored and processed in regions that comply with your local data protection regulations.
- What Does the Company Do with My Data?: Review the terms and conditions of any freeware AI tool to understand how your data will be used.
- Data Privacy and Security: Ensure that the freeware AI tool has robust security protocols to protect your data from unauthorized access and breaches.
Next Steps for Organizations
Now that we understand the importance of data classification and access control, here are some actionable steps your organization can take:
- Conduct a Data Inventory: Identify and catalog all data assets within your organization. Determine the sensitivity and criticality of each data type.
- Define Classification Categories: Establish clear classification categories based on sensitivity, regulatory requirements, and business criticality.
- Implement Access Controls: Apply appropriate access control mechanisms to ensure that only authorized users and AI systems can access sensitive data.
- Train Employees: Educate your staff about data classification policies and access control procedures.
- Monitor and Audit: Regularly monitor data access and usage. Conduct audits to ensure compliance with data classification and access control policies.
Conclusion
Effective data classification and access control are cornerstones of robust data security practices. By categorizing data based on sensitivity, regulatory requirements, and business criticality, and by implementing stringent access controls, organizations can better protect their assets, ensure compliance, and minimize risks. Additionally, being cautious about the AI tools you use and understanding their data processing practices can further safeguard your data.
Thank you for your attention. I'm now open to any questions you might have.
If you want to know more about CompTIA or Cybcr Security feel free to contact me:
Contact me via,
Mail: tycho.loke@peoplerock.nl
Phone: +31 6 39 41 36 65
LinkedIn: Tycho Löke

