Microsoft expands MFA with number matching

Microsoft has enhanced its multi-factor authentication app, Authenticator, with features such as number matching and additional context regarding login attempts. These new functions are designed to prevent accidental approval of malicious login attempts.
Microsoft has made improvements to its multi-factor authentication app, Authenticator. Users can now enter a two-digit number when logging into their Microsoft account, replacing the previous method of selecting from three displayed numbers. This feature is intended to reduce the risk of accidental approval of malicious login attempts.
Microsoft initially announced this function last year and has now made it widely available to administrators. By allowing users to enter the number themselves, Microsoft believes it to be more secure, especially with the increasing trend of MFA abuse and user MFA fatigue.
In addition, the Authenticator app can now provide more context regarding login attempts, such as the location and app used. This new feature can help to prevent malicious MFA login attempts from being accidentally approved.
Administrators can choose whether users enter the numbers or choose from three displayed numbers, but this option will be removed in February next year. These features will be set for all users at that time. The Microsoft Authenticator app is widely used by businesses and consumers alike for secure login to their Microsoft accounts.
Refreshed Admin UX and APIs
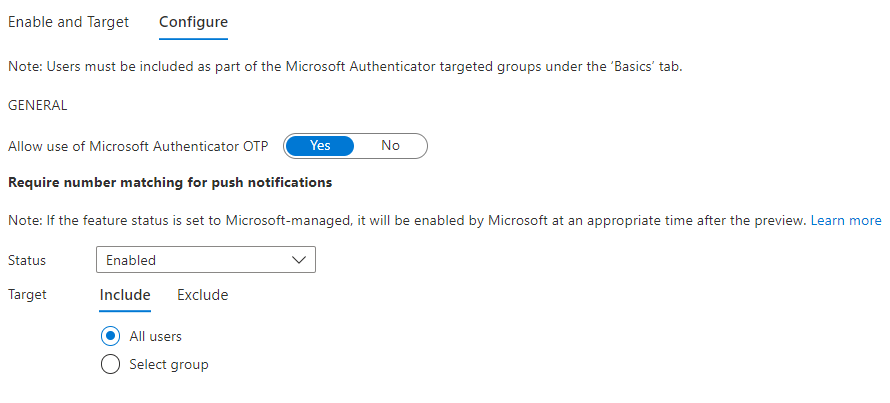
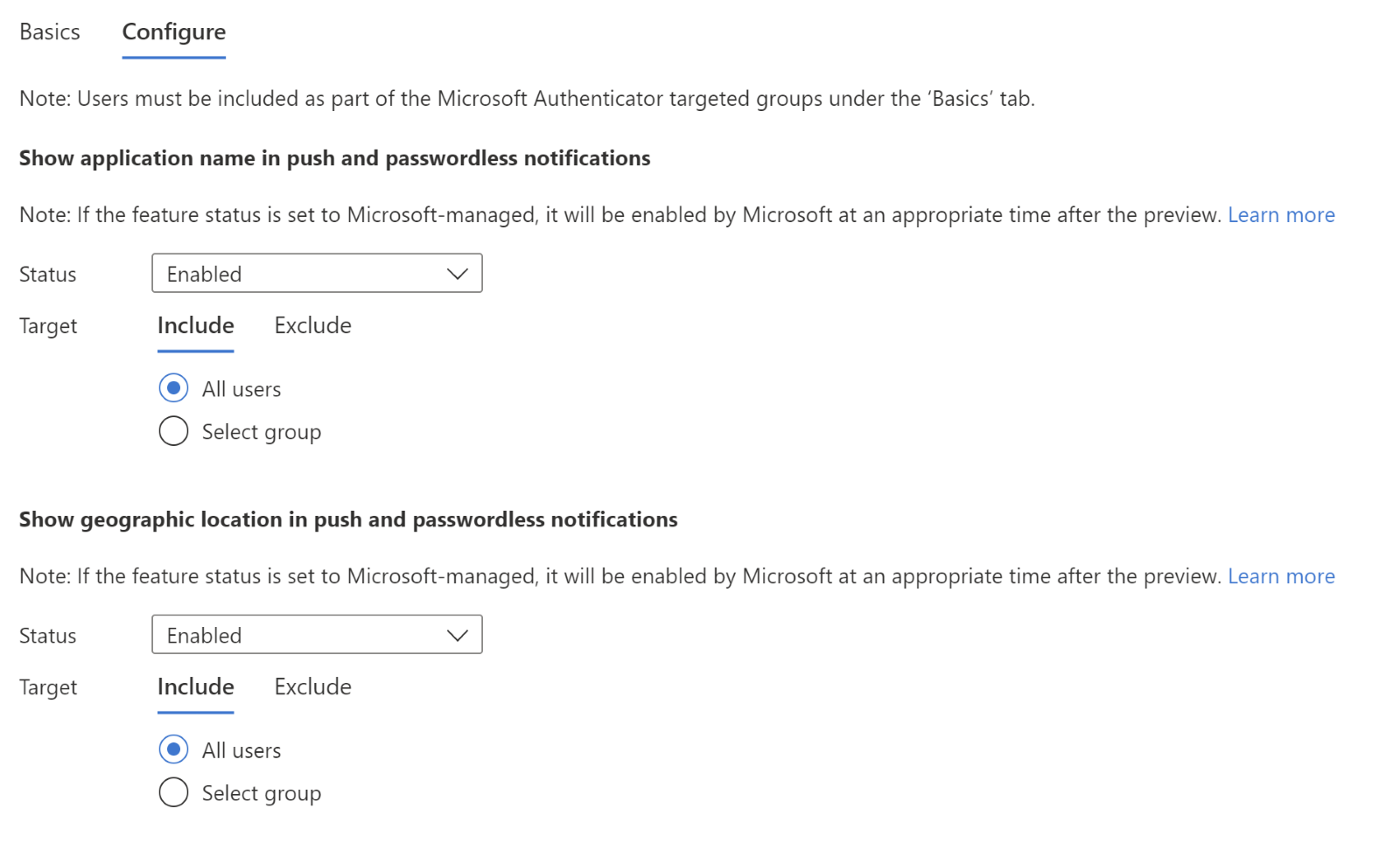
Admins can now better manage their Microsoft Authenticator app features with our refreshed Admin UX and APIs. Use the new “Configure” tab in the Admin UX to enable/disable different features. It now also includes the highly requested capability to exclude groups from features to assist with smoother feature rollouts.
Showcase of what it will look like
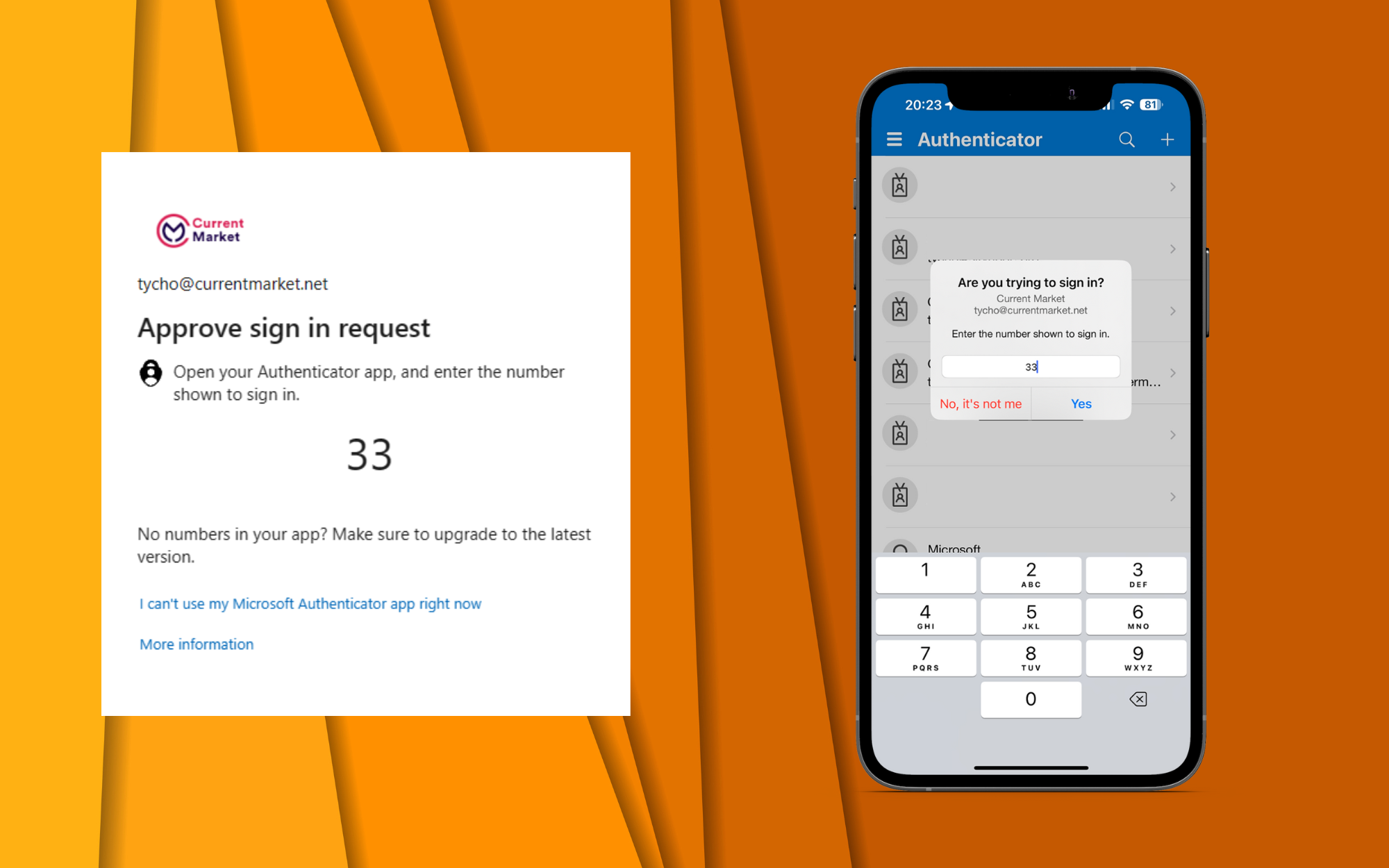
Here is a quick preview using the tenant from Current Market on what the new notification will look like within the desktop and mobile authenticator app.
How to Install MFA Number Matching in your tenant
To enable number matching in the Azure AD portal, complete the following steps:
- In the Azure AD portal, click Security > Authentication methods > Microsoft Authenticator.
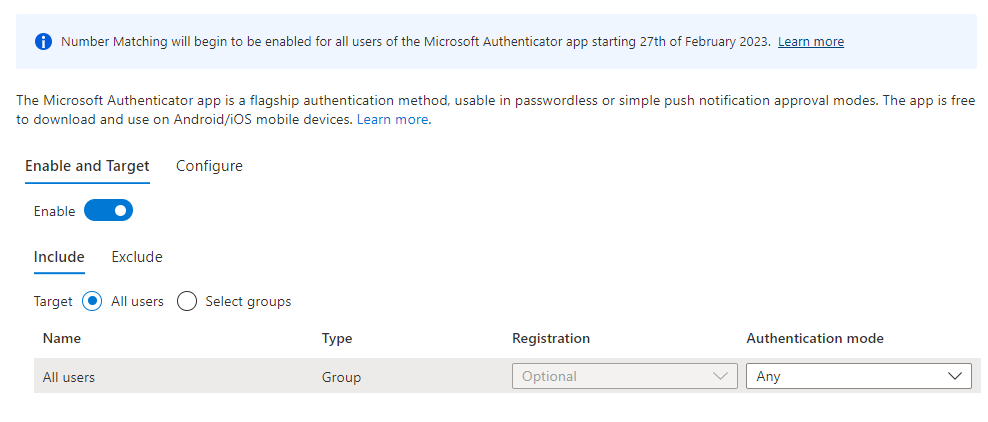
2. On the Enable and Target tab, click Yes and All users to enable the policy for everyone or add selected users and groups. Set the Authentication mode for these users/groups to Any or Push.
Only users who are enabled for Microsoft Authenticator here can be included in the policy to require number matching for sign-in, or excluded from it. Users who aren't enabled for Microsoft Authenticator can't see the feature.
3. On the Configure tab, for Require number matching for push notifications, change Status to Enabled, choose who to include or exclude from number matching, and click Save.