Unlocking the Power of Cross-Tenant Synchronization (preview)

Managing external users has always been a challenge for organizations, especially when it comes to Identity Governance. Microsoft Entra has introduced a new feature called cross-tenant synchronization, which has been highly anticipated by community members and organizations alike. This feature aims to bridge the gap and simplify the management of guest users. In this blog post, we'll explore the key features of cross-tenant synchronization and how it works. We'll also provide step-by-step instructions on how to enable this feature so that you can take advantage of its benefits. So, let's dive into the world of cross-tenant synchronization and unlock its potential in your organization's Identity Governance strategy.
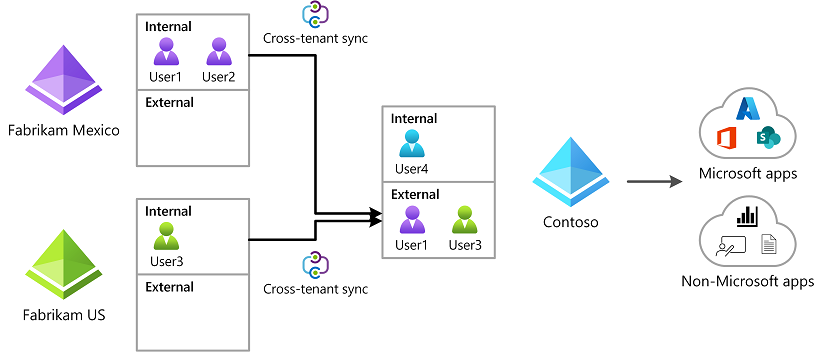
What is Cross-Tenant synchronization and what do you need to know for it?
Cross-tenant synchronization is a new feature that simplifies collaboration between multiple Microsoft 365 tenants by automating the creation, updating, and deletion of Azure AD B2B users across multi-tenants. This feature has been designed to solve the challenges that organizations face while managing external users, also known as guest users, and streamlines the identity governance process.
To use cross-tenant synchronization, you need an Azure AD Premium (P1 or P2) license for each user you wish to synchronize, as well as either a Hybrid Identity Administrator role or a Global Administrator role. Inviting external users from other organizations to collaborate on Microsoft applications such as Teams, SharePoint, or third-party applications like Salesforce or ServiceNow, requires an invitation process that can be cumbersome and often leads to issues with life-cycle management.
With cross-tenant synchronization, changes to guest user accounts such as a name change, department change, or when an employee leaves the organization, can be automatically synchronized across tenants. This feature offers a push process from the source tenant and requires configuration in the source tenant before use.
It's important to note that cross-tenant synchronization won't replace B2B direct connect and that the default UserType will be Member instead of Guest. The feature also detects existing B2B users and avoids creating duplicates. To use cross-tenant synchronization, it's necessary to set up synchronization in the source tenant where the identity is managed.
In conclusion, cross-tenant synchronization is a powerful new feature that simplifies collaboration between multiple Microsoft 365 tenants, improves identity governance, and reduces the burden on administrators managing external users. Users created by cross-tenant synchronization will have the same experience accessing Microsoft Teams and other Microsoft 365 services as B2B collaboration users created through manual invitation.
How to configure cross-tenant access settings?
Configuring Cross-Tenant Access Settings for User and Group Synchronization
To synchronize users and groups between two tenants, the source and target tenants, it's essential to configure cross-tenant access settings. This process involves creating a trust between the two tenants to establish a secure connection.
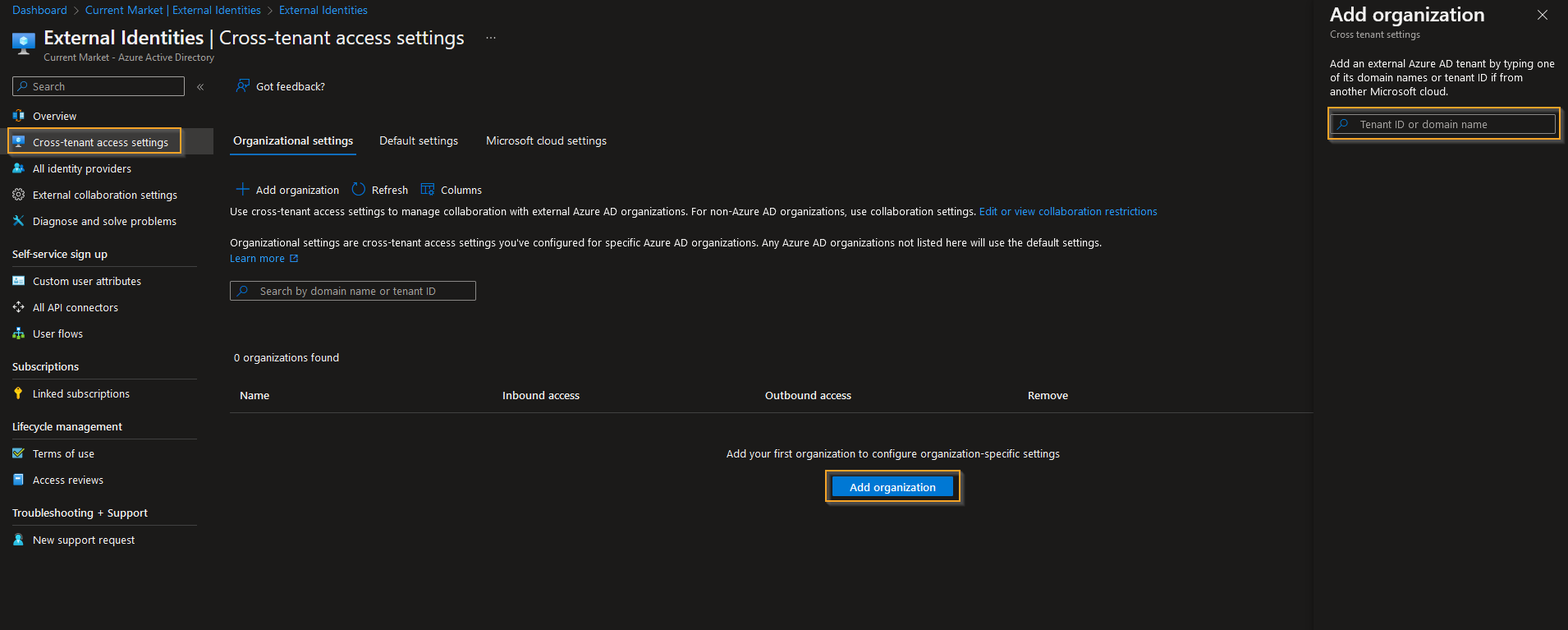
To get started, navigate to the Azure Portal or Entra Portal for the source tenant, click External Identities, and select Cross-tenant access settings. From there, click Add organization and enter the domain or tenant ID of the target tenant to add the external Azure AD tenant. It's crucial to follow these steps to avoid permission errors.
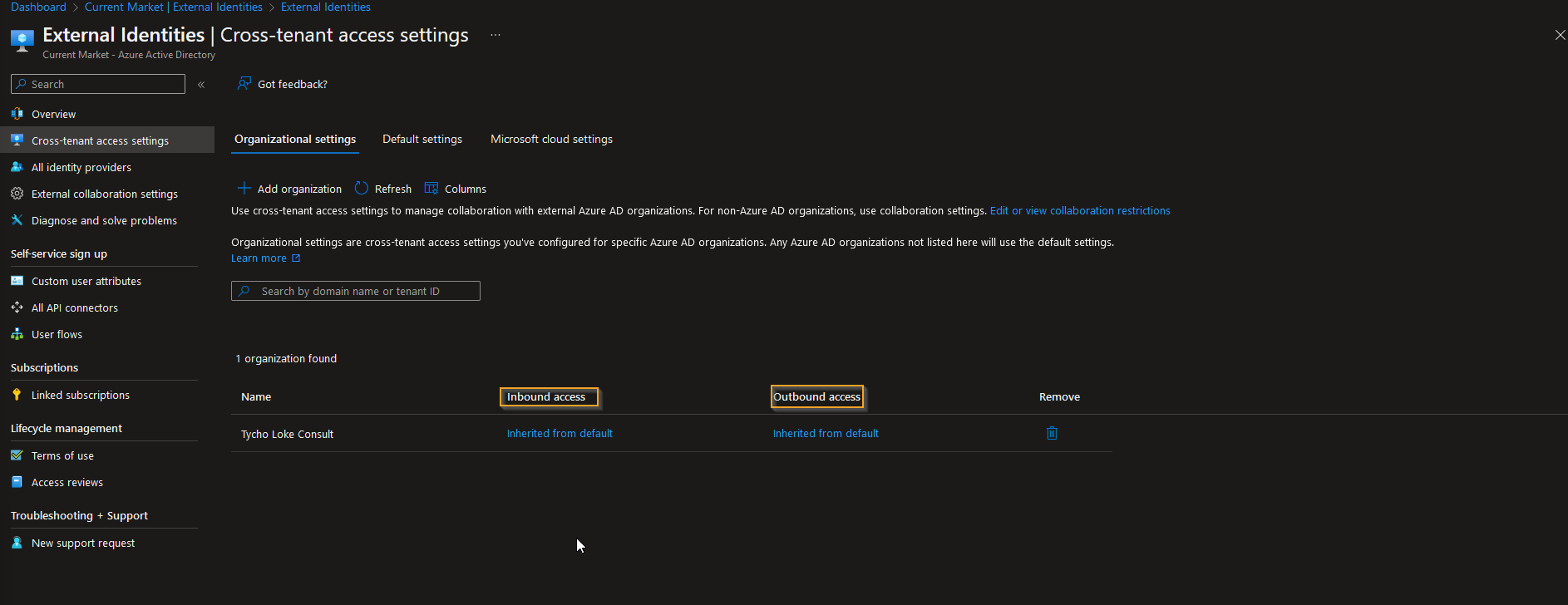
After adding the target tenant, we need to modify the Outbound access settings since we'll be syncing users from the source tenant. The same process should be followed for the target tenant, but this time we need to modify the Inbound access settings for the target tenant.
By configuring cross-tenant access settings, we establish a trust relationship between the source and target tenants, enabling us to synchronize users and groups smoothly. This trust relationship provides a secure connection and is essential for the successful implementation of cross-tenant synchronization.
In- and Outbound cross-tenant settings
When setting up cross-tenant synchronization, it's essential to understand the various configuration options available to ensure a successful synchronization process. One critical aspect to consider is the Inbound access cross-tenant setting, which contains several tabs that allow us to fine-tune our synchronization process. In this blog post, we'll focus on two of these tabs: the "Trust settings" and "Cross-tenant sync" options.
Cross-Tenant Sync
To enable user synchronization from the source tenant to the target tenant, it is crucial to select the "Allow users sync into this tenant" option in the Inbound access cross-tenant settings. Without checking this option, user synchronization between the two tenants will not be possible.
Additionally, in the Outbound access cross-tenant settings, it is important to ensure that the "Suppress consent prompts for users.." option is enabled in the Trust settings tab. This allows for a seamless user experience without requiring users to repeatedly provide consent for accessing resources in the target tenant.
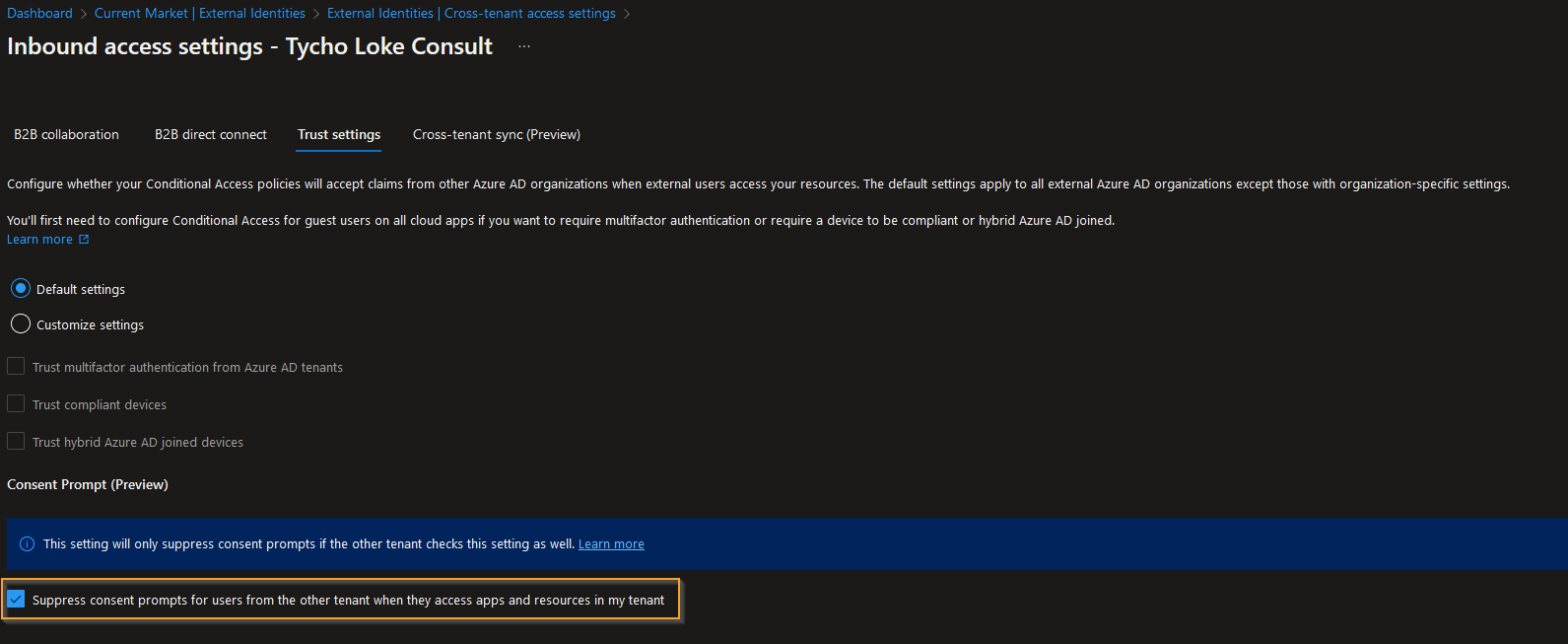
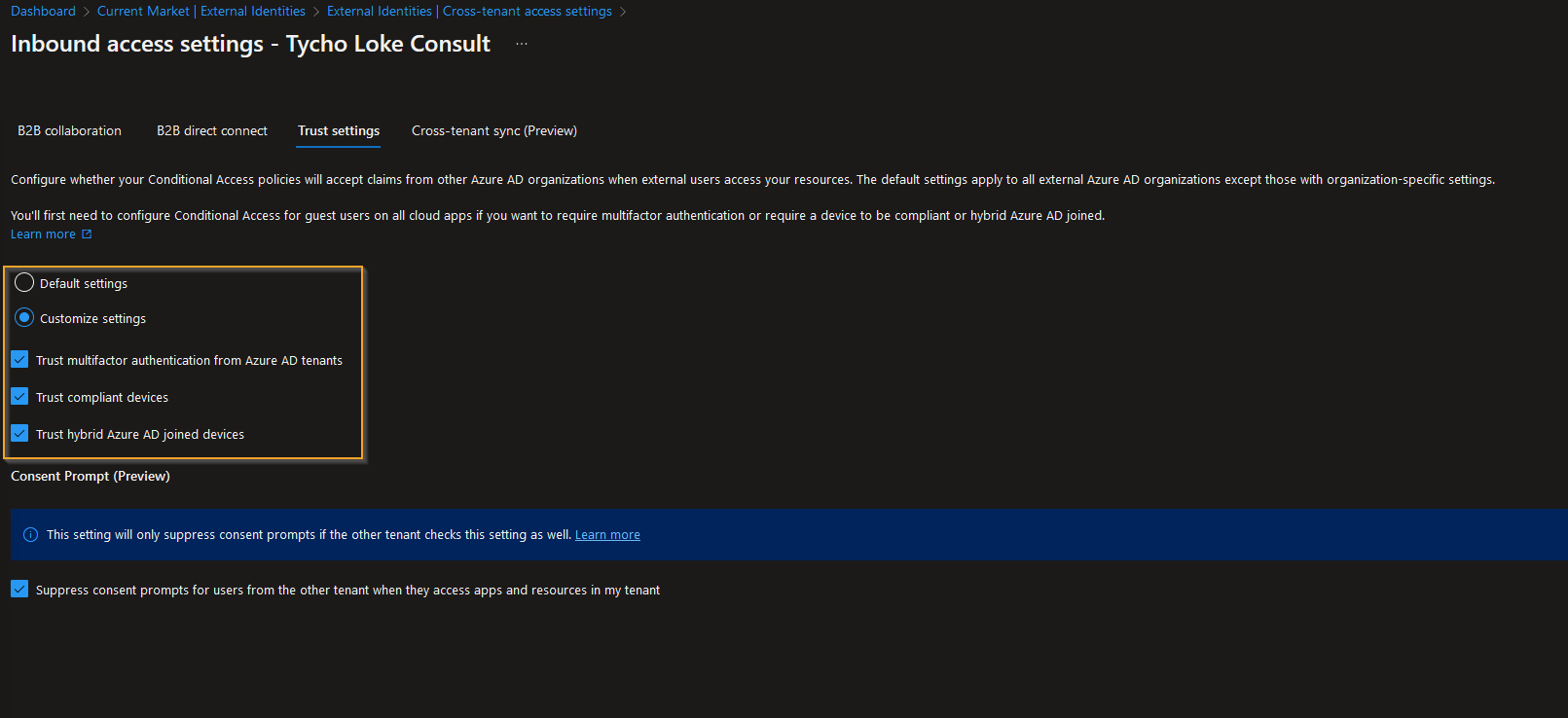
Trust Settings
To provide a seamless user experience for users accessing resources in the target tenant, it is highly recommended to select the "Customize settings" option within the "Trust settings" tab and choose all available options. By doing so, users will not be prompted for MFA as soon as they access the target tenant. In terms of compliance, once a device is trusted in the source tenant, it will automatically be trusted in the target tenant as well.
Another key setting to consider is suppressing the Consent Prompt. Users do not want to be bothered with repeated prompts for accessing resources. Make sure this setting is properly configured in the source tenant to avoid any disruptions in user experience.
How to Configure Cross-Tenant Sync?
Now that the trust has been established between the source and target tenants, we can proceed with the configuration process. It is important to note that if the above steps were not followed, errors may occur during the configuration.
- Navigate to the Azure Active Directory portal or the Microsoft Entra Portal in the Source Tenant.
- Click on the Cross-tenant synchronization (Preview) blade.
- Select the Configurations blade and click on New configuration to create a 1 to 1 synchronization between the source and target tenant.
- Provide a name for the configuration and click on Create. For example, you can use "Cross-tenant A" as the configuration name.
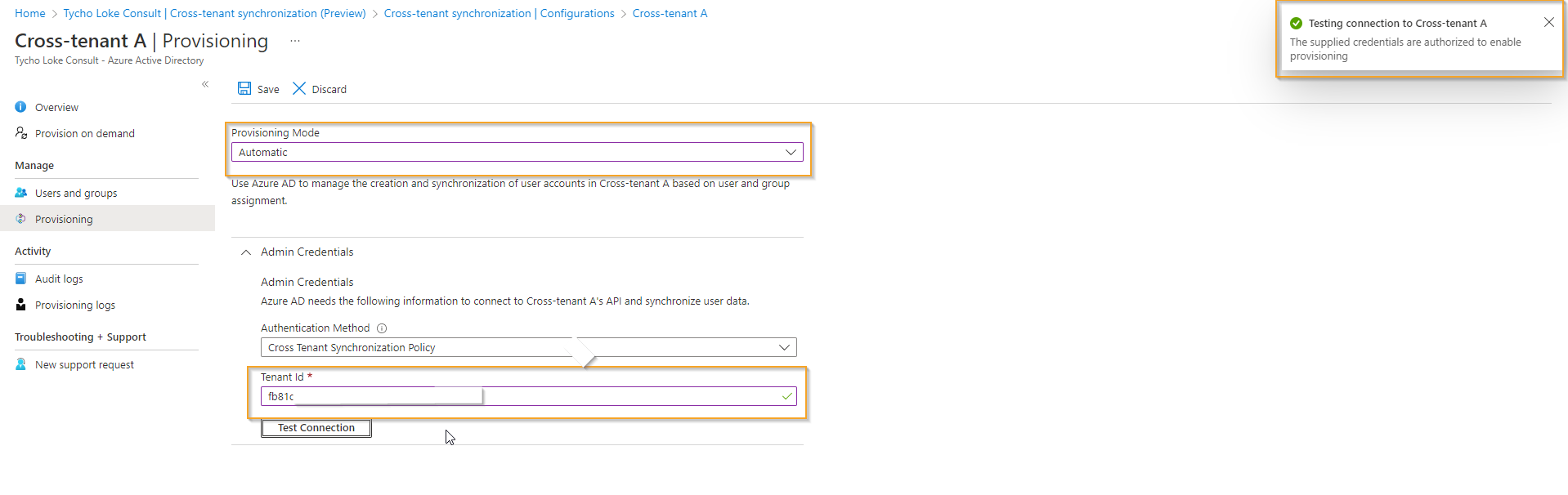
- Click on the configuration you have just created and select Provisioning. Set the Provisioning Mode to Automatic instead of Manual to validate the synchronization.
- Provide the Tenant ID of the target tenant, click on Test connection, and Save. Note that you do not need to provide credentials as a trust has already been established between the two tenants.
- At this point, no synchronization will start, but you have validated that the configuration is set up correctly.
Provisioning
Mapping
The mappings configuration is an essential step after the validation process. You may need to adjust these mappings for various reasons such as:
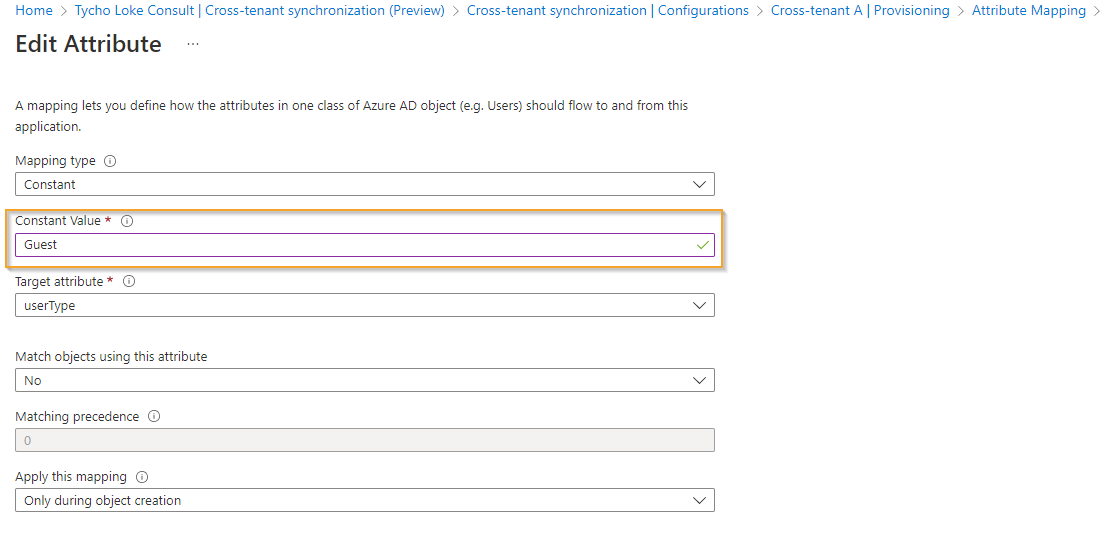
- The users/objects synced using this feature are identified as Member Type "Member" rather than "Guest," which can lead to different treatment in cases such as Conditional Access or Access reviews.
- If a user was previously invited to the target tenant, it won't synchronize or apply since the default mapping is set to "Only during object creation."
It's important to keep in mind that changes to attribute mappings may affect existing users when synchronizing new objects. To modify the attribute mappings, go to the "Provision Azure Active Directory Users" option and review the list of attribute mappings. For instance, to change UserType from Member to Guest, click on the Value Member and change the Constant Value to Guest. Once you start your first synchronization, the user will be synced as UserType Guest.
OTHER SETTINGS
Additional synchronization settings can be configured to customize the synchronization process further. This includes setting up alerts, defining a threshold to prevent accidental deletions, and specifying the synchronization scope. By default, only the assigned users and groups are synchronized, but this can be adjusted to fit the needs of the organization.
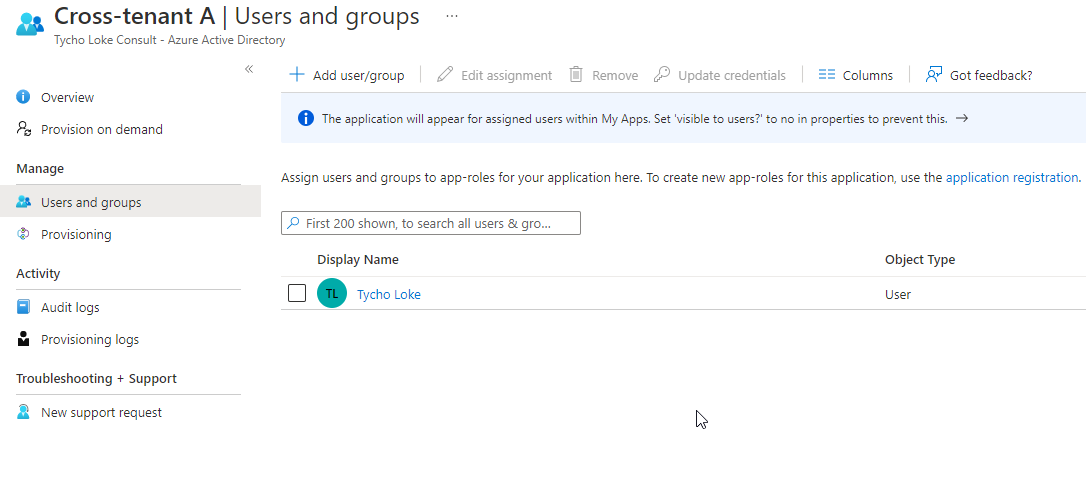
USERS AND GROUPS
Within this section, you have the option to add Azure AD users and groups that you wish to synchronize with the target tenant. As an illustration, for the purpose of this blog post, I will proceed to synchronize Tycho Loke.
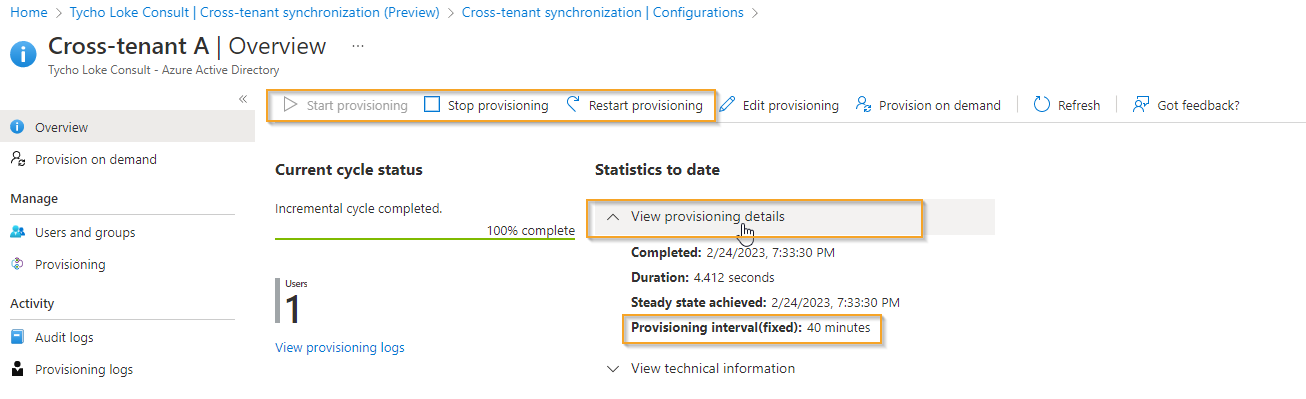
Provisioning
After configuring all the settings, we can initiate our first provisioning. Navigate to the Overview blade and select "Start provisioning" to begin. You can check the interval (default 40 minutes) by clicking "View provisioning details." If you need to start a provisioning immediately, use the "Restart Provisioning" option.
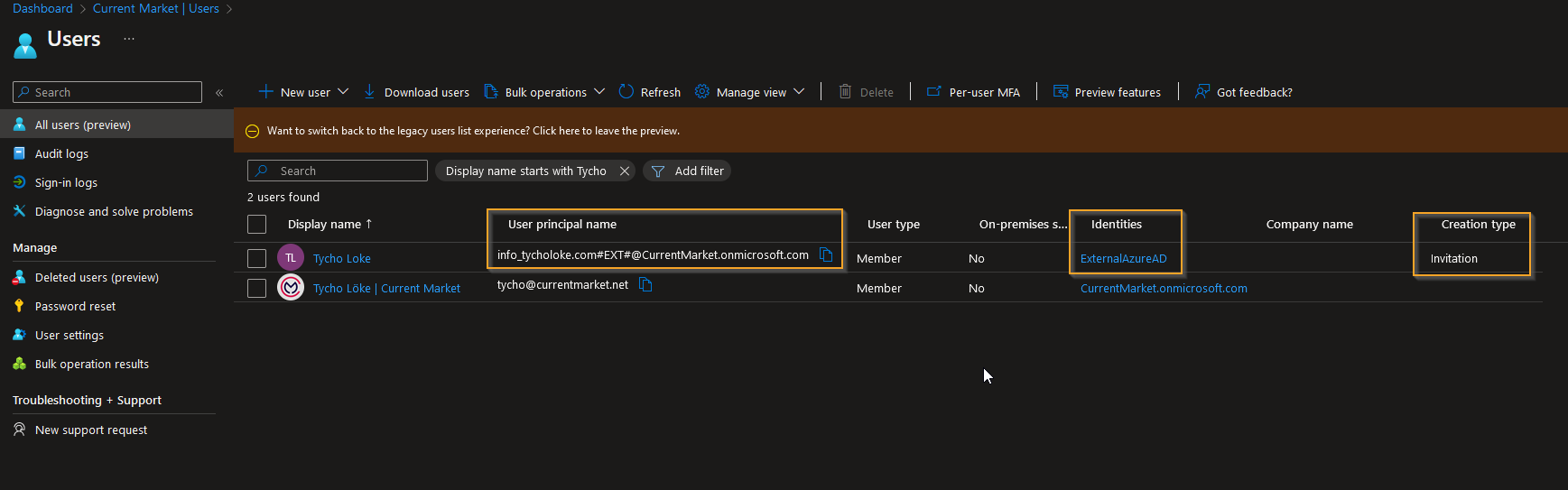
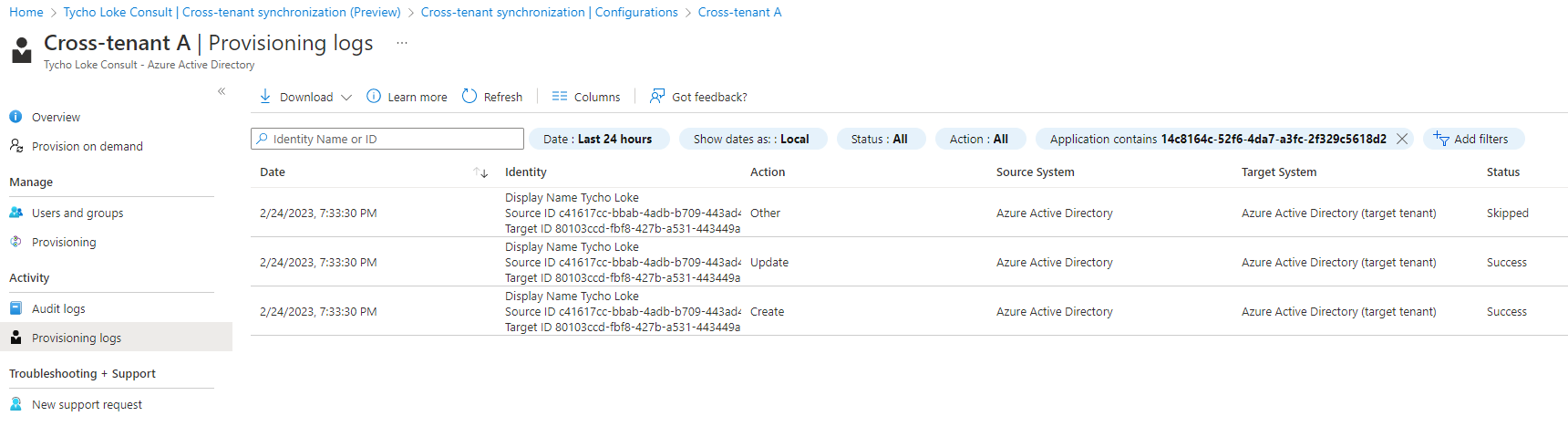
Provisioning Logging
When we check the synchronization log, we can get a detailed view of the synchronization process. This includes whether the user was created, updated, or skipped due to any issues. By clicking on an entry, we can view the steps taken during the process, along with any recommendations or troubleshooting information, modified properties, and a summary of the synchronization.
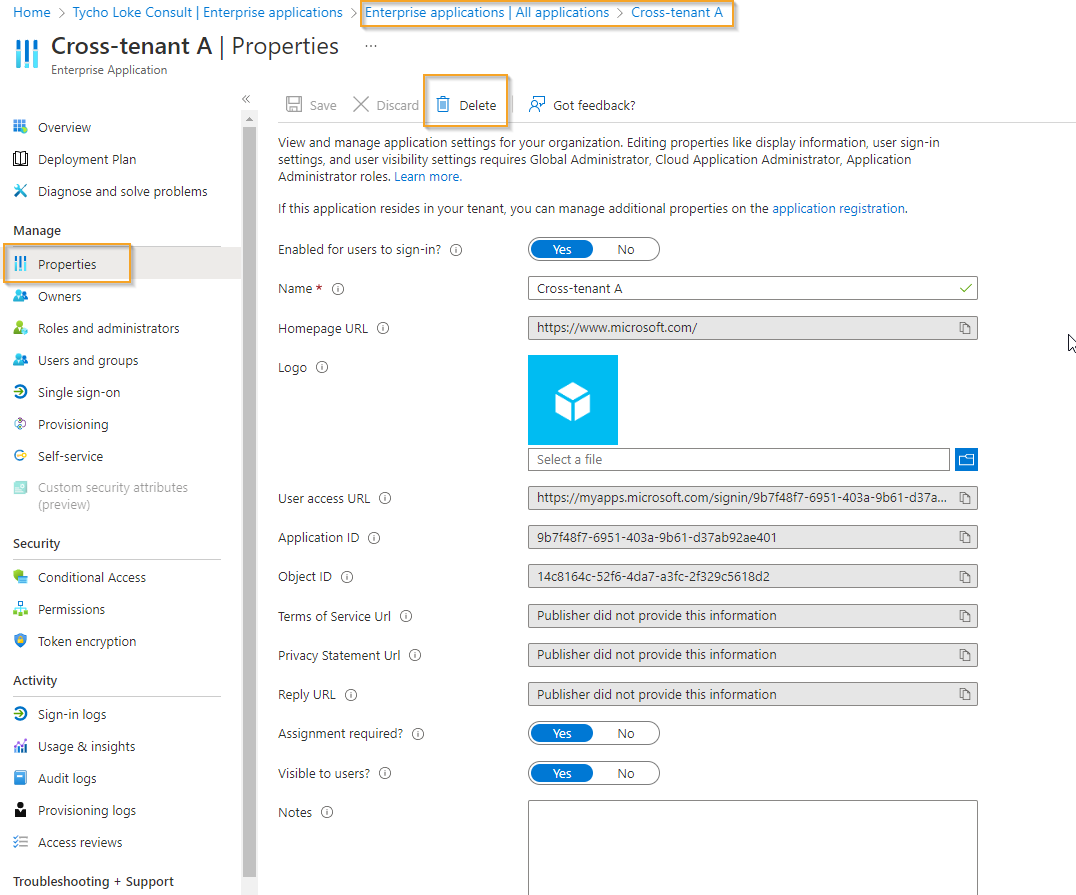
How to remove the cross-tenant sync configuration?
To remove the configuration we created in the previous step, simply navigate to the Enterprise Applications blade. You can find this option under the Applications blade in the Microsoft Entra Portal.
Sources

If you require further assistance, please don't hesitate to contact me.
Contact me via,
Mail: tycho.loke@peoplerock.nl
Phone: +31 6 39 41 36 65
LinkedIn: Tycho Löke

